When migrating to the cloud, companies face challenges governing their data and security. In the field of cloud computing, a landing zone is a basic foundation for further cloud deployments. AWS Control Tower is a managed service to implement such a landing zone in a fast and standardized way.
In this article, I will describe:
Main Challenges
Let’s imagine a company organizational structure is made up of teams such as finance, marketing, security, developers, operations, and so on. Each team has certain activities to achieve goals, functionalities, and the processes that guide them cross-functionally. As the company gets bigger, the activities increase, the size and functionality of the teams increase, and new departments come up with new use cases. At the top of the company is a general manager who governs everything, therefore the need for a centralized and well-controlled structure will arise so that everything works perfectly. The same workflow affects our environments, systems, and applications in on-premise or cloud. Due to a large number of applications, systems, and teams, enterprise companies are facing the challenges to manage and govern all of them safely in the cloud.
Landing Zone Capabilities
In my experience with enterprise companies, one of the biggest challenges is how to find a simple, strategic solution to govern the systems and data in a secure, scalable, and efficient way. They are truly looking for a full-scope process while keeping their systems under control, such as who can access what and when, if there are security and vulnerability scanners in place, regulatory auditors, etc.
A cloud landing zone is a centralized management solution of accounts, services, and processes between them. Each account or service has certain activities and functionalities, which are governed by centralized governance. Typically, a landing zone offers:
AWS Control Tower
In our case, the control tower is not a building on the airport, but a service managed by AWS. It offers a highly effective governance solution by providing an automated way of implementing a cloud landing zone.
What does Control Tower offer?
Purpose
Over time, AWS has carefully curated a best practice for landing zone solutions. Control Tower is a managed service to facilitate landing zone setup and ongoing management, and to govern a secure compliance multi-account and services, and access management using an established blueprint. Providing a range of services and mechanisms for different purposes, such as ensuring 24/7/365 monitoring of critical systems, allowing traceability in real-time, audit actions and changes to systems, performance improvements, real-time alerts, and potential outage preventions, offer greater reassurance and efficiency. In the previous blog, I detailed Setting Up an AWS Landing Zone with Control Tower – check it out now if you haven’t already.
Features and capabilities
You can set up a Control Tower in a centralized management account within a few hours. You only need to enter two emails, one linked to a logging account and the other one to an audit account. Both emails must not be linked to an existing AWS account, otherwise it will fail. Within two hours you will see a full setup of an AWS landing zone as is described in the image below.
Account structure and services
The image below lists the AWS services linked to each account. From the orange line and above, all services are created automatically during the Control Tower setup and all of them are part of the AWS landing zone solution. Below the orange line may be the services you can add in the landing zone for future purposes or you can add an account based on your needs.
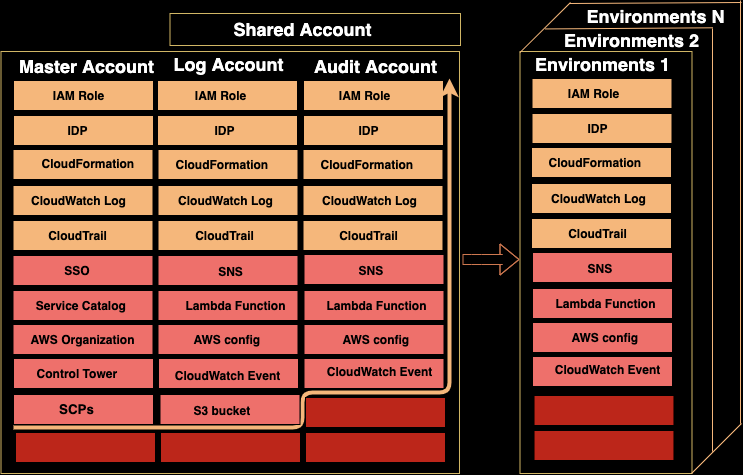 Basic Landing Zone provided by Control Tower
Basic Landing Zone provided by Control Tower
Let's see all the AWS services provided in each account and the relationship between them:
AWS Services deployed to all accounts
In the first part of the table are services such as: CloudFormation, IDP, IAM roles, CloudWatch, and CloudTrail, all of which are being deployed to all accounts because they help to connect and grant permissions through accounts and services and to perform certain operations automatically. Also, they make sure that monitoring is in place. Let's see what their purposes are:
AWS CloudFormation templates — These are established blueprints provisioned by AWS that allows Control Tower to automatically setup accounts and services. These models describe resources in JSON format and there is in-place versioning control.
Identify Provider (IDPs) —This allows accounts to grant permission on cross-account resources. These services are applied to all accounts.
IAM Roles— This defines a set of authorizations and they are associated with different entities. Below are the three most common types created by Control Tower.
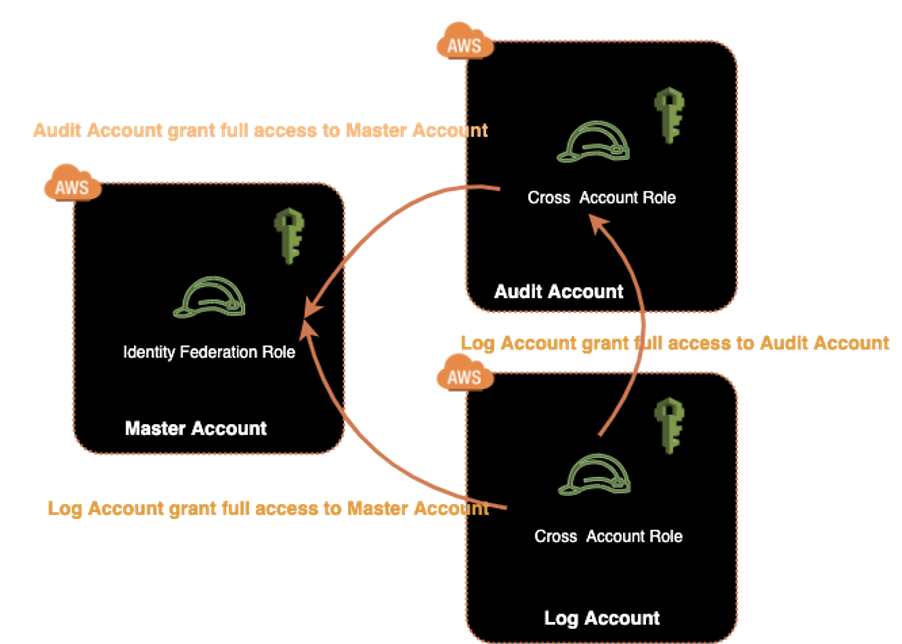 IAM Roles cross-account
IAM Roles cross-account
CloudWatch logs — The scope of this service is to monitor the infrastructure, network, and applications, and take control in case of detection. All of the services that are part of the landing zone generate the metrics and send these metrics to CloudWatch.
CloudTrail — This service also is used for monitoring but has a different scope. It allows you to collect all the history of API through AWS Management Console, AWS SDKs, and command line.
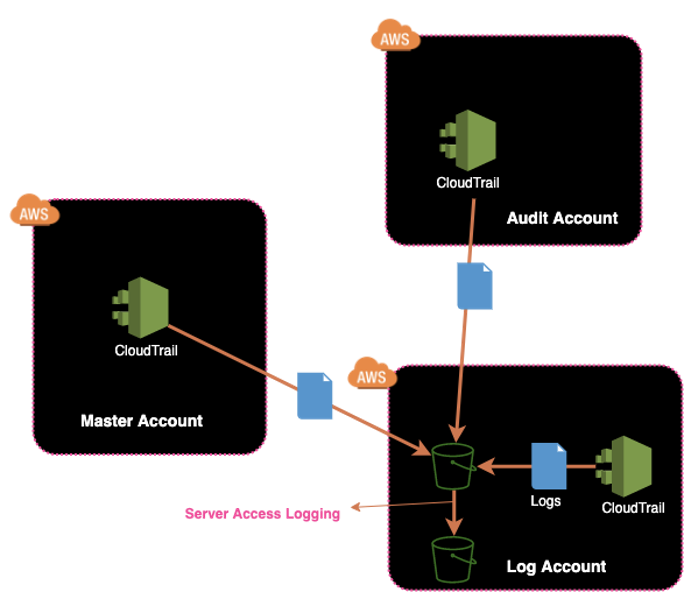 CloudTrail
CloudTrail
Services applied to a master account
Those services are deployed only to the master account because their purpose is to govern and manage systems and processes in a secure and scalable way. Let’s review them.
Single Sign-On (SSO) — This allows you to centrally access management and permission to AWS accounts. You can authenticate an AWS account with a single user and password through a custom, friendly link provided by SSO. Also, you can setup user permissions, account permissions, group permissions, and session duration preferences. Centralized access management avoids creating IAM users and permissions in child accounts.
Service Catalog — This allows you to provision portfolios and add the product based on requirements and the specified budget. Control Tower creates its portfolio with an already associated product: “AWS Control Tower Account Factory.” By default there is no budget specified. If you want to launch a new account part of Control Tower, you can do it through Account Factory.
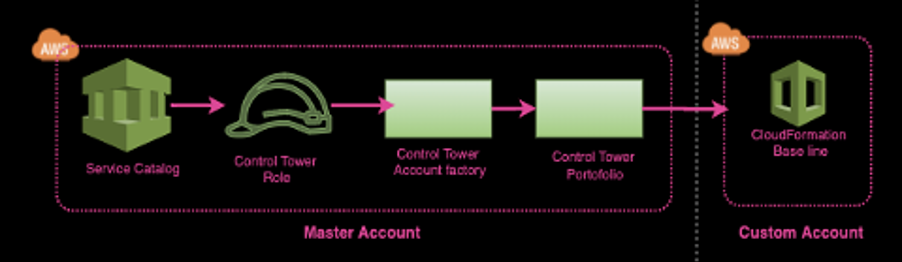 Service Catalog
Service Catalog
AWS Organization — It is used to set up an account organization structure in groups. In each of them, you can apply a service control policy (SCP), ensuring that accounts stay within your organization's access control guidelines. Control Tower creates three groups (root, core, and custom). Core and custom are under root. Accounts log and audits are part of the core unit organization. But you also can extend this structure, adding more organization units and accounts.
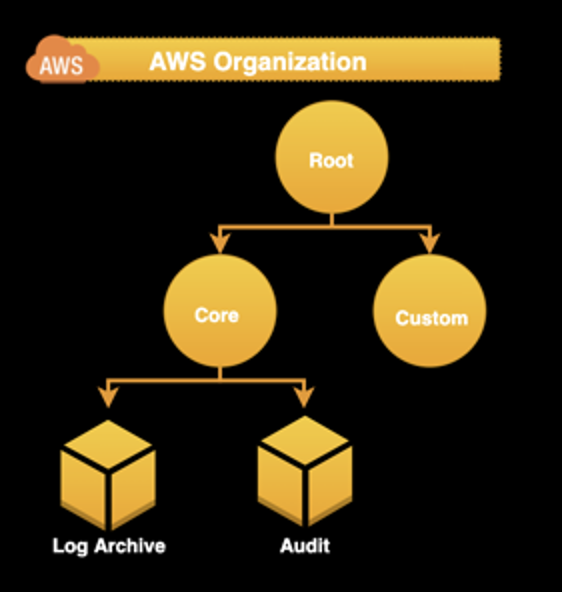 AWS organizations units
AWS organizations units
Guardrails—There are some basic security and compliance rules that are part of the baseline deployed to all new accounts automatically to prevent and detect certain resources from behaviors that don't match the rules, and they become non-compliant.
Services applied to shared accounts
The purpose of the log account is to collect all the logs between accounts and regions. The purpose of the security account is to audit environments and services by following the protection rules.
AWS Config — This allows you to create rules on how to deploy a specific AWS service. In the case that they don't follow the rules, this ensures that the service doesn't become a complaint.
AWS CloudWatch Event Rules —This allows you to create a rule to trigger an AWS service based on a custom schedule.
AWS SNS —This service is used for notifications.
AWS Lambda Function —This service allows you to run your code.
Now let’s see how these services work together in the solution provided by the Control Tower. The following workflow shows when the S3 bucket in log and audit account becomes non-compliant based on the guardrail’s rules. Let’s review the steps.
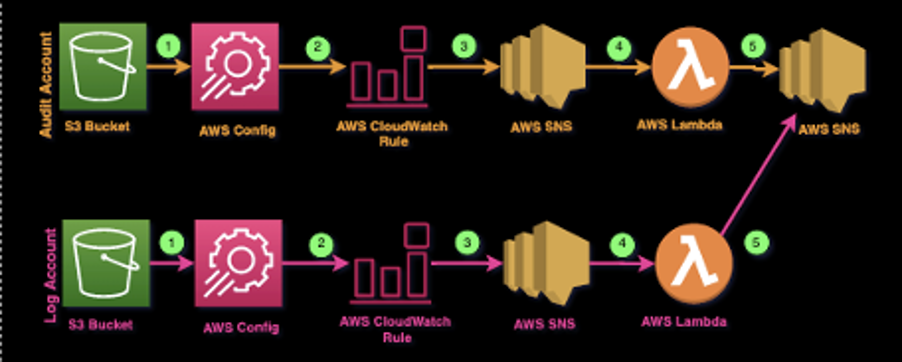 Guardrails setups
Guardrails setups
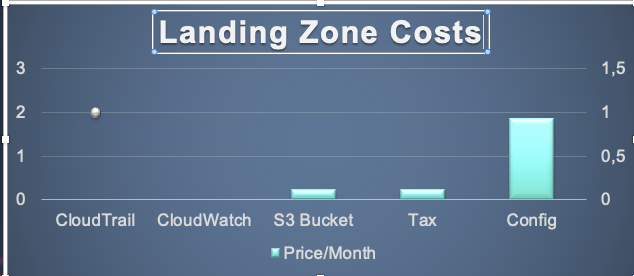
Costs
The landing zone created by Control Tower uses AWS resources and therefore generates some costs. For a newly created standard landing zone, this is expected to be:
Next Steps
In summary, Control Tower offers a good multi-environment, access management, network design, and logging strategy solution. It allows you to automate using established blueprints, having the guardrails in place to ensure that all of them are deployed following the policies and rules. It's a good starting point and, as your company grows, you can extend the landing zone solution by adding more environments, applications, security, and rules based on your needs and requirements. In many cases, Control Tower can help you to get to the cloud quickly and safely. However, Control Tower is a basic standard solution, so it might not fit all your specific needs. In the picture below I specify some limitations.
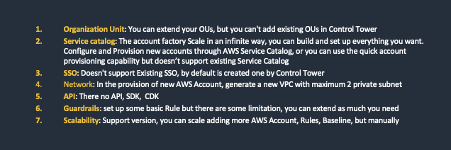
If required by your use case, Mobiquity can help you to meet your needs, either by extending Control Tower or with a custom landing zone design for full flexibility.
Give us your information below to start the conversation.
